Email and phishing scams are among the most common and dangerous cyber threats that you may encounter online. They are designed to trick you into opening, clicking, downloading, or sharing something that can compromise your security and privacy. But how do you spot and avoid email and phishing scams in 2023?
In this blog post, let’s discuss some tips and insights on how to spot and avoid email and phishing scams in 2023 and onwards. We will also explain what email and phishing scams are and how they work, what are some common types and examples of email and phishing scams, what are the potential consequences of falling for them, and how AI can be used for or against them.

Table of Contents
What are Email and Phishing Scams?
Email and phishing scams are fraudulent emails or messages that pretend to be from legitimate sources, such as your bank, your employer, your friend, etc., and ask you to do something that can harm you or benefit them. For example, they may ask you to:
- Confirm or update your personal or financial information
- Pay an invoice or a bill
- Log in to a website or an app
- Open an attachment or a link
- Send money or gift cards
- Download a software or an app
The goal of email and phishing scams is to steal your identity, money, data, or device. They use various techniques to make their emails or messages look convincing and authentic, such as:
- Spoofing: Using fake or similar sender addresses or domain names
- Social engineering: Using psychological tricks to manipulate your emotions or behavior
- Malware: Using malicious software or code to infect your device or network
- Phishing kits: Using ready-made templates or tools to create fake websites or forms
According to Cofense Email Security Review: Q3 2022³ , email and phishing scams accounted for 96% of all cyberattacks in the third quarter of 2022. The most common types of email and phishing scams were:
- Business email compromise (BEC): Targeting employees or executives of a company and impersonating their colleagues, partners, or clients
- Invoice fraud: Targeting businesses or individuals and sending fake invoices or bills for goods or services that were never delivered or requested
- Fake login pages: Targeting users of popular websites or apps and redirecting them to spoofed login pages that capture their credentials
- COVID-19 related scams: Targeting people who are affected by the pandemic and offering fake vaccines, tests, treatments, donations, etc.
Some examples of real email and phishing scams
Example 1: A BEC scam that impersonated a CEO of a company and asked an employee to buy gift cards for a client. Source: Cofense
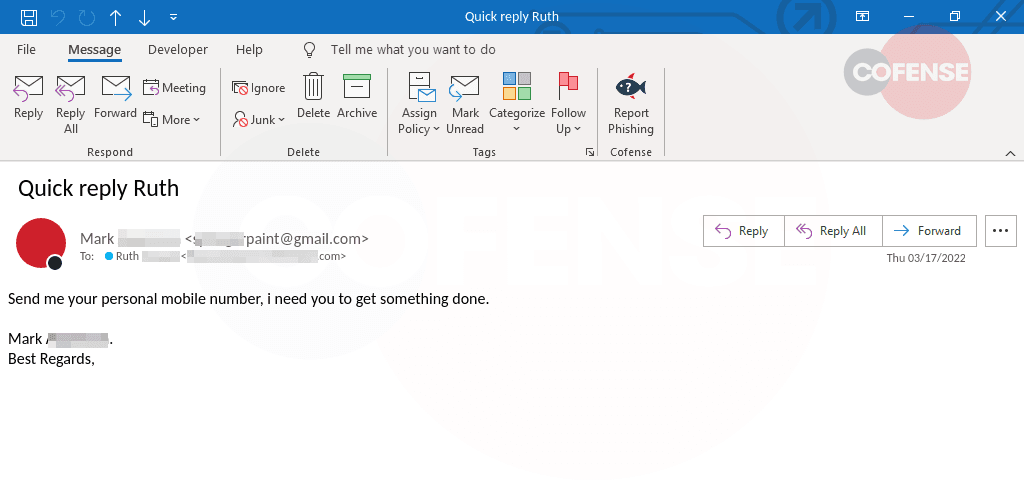
Example 2: An email customized with the recipient’s email address (redacted) and the current date in the subject. Source: Cofense
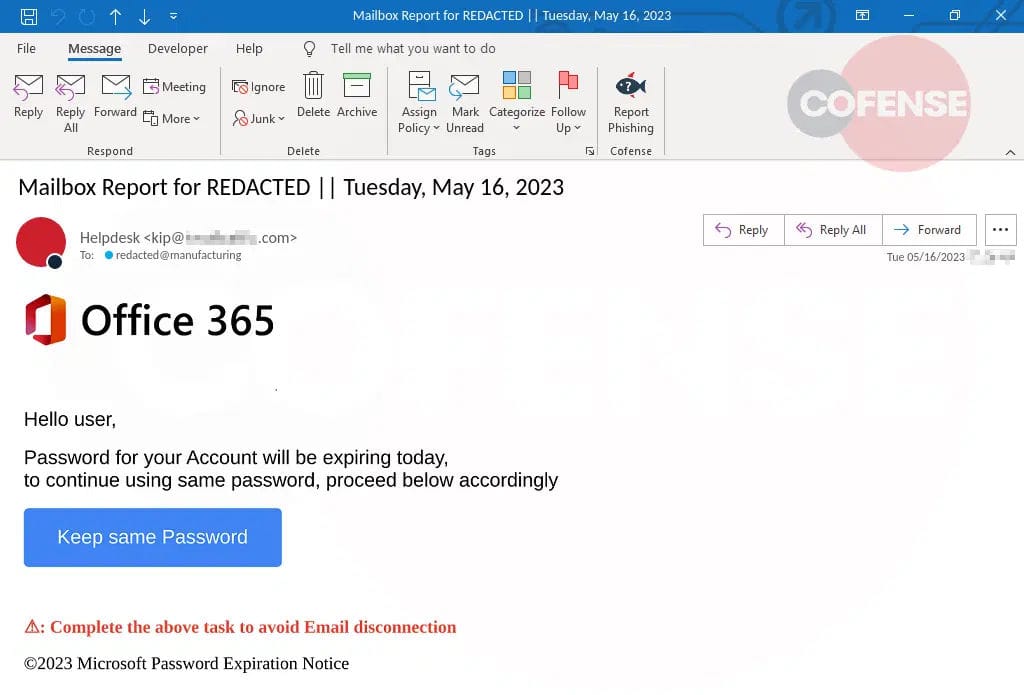
Example 3: A screenshot of the recent phishing email used to deliver Gh0st RAT via an embedded link. Source: Cofense
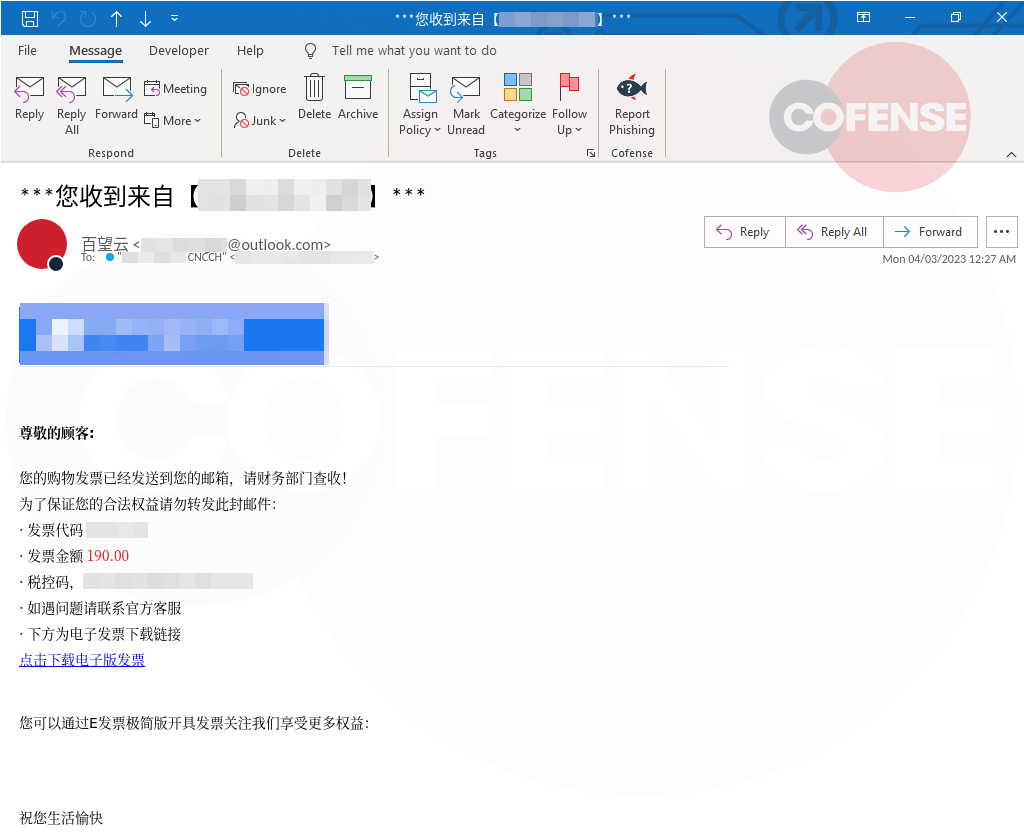
Example 4: How scammers can invoice you via PayPal. Source:Make use Of

Example 5: You can study 16 more examples of scams hitting businesses from the Tessian blog
As you can see, these email and phishing scams look very convincing and authentic. But they are not. They are designed to deceive you and harm you. That’s why you need to know how to spot and avoid them.
How AI Can Be Used for or Against Email and Phishing Scams
AI is a powerful technology that can be used for good or evil. It can be used to create, detect, prevent, or enhance email and phishing scams. With the rise in the use of AI technology, scams with the aide of AI are sure to increase.
On one hand, AI can be used to create more sophisticated and realistic email and phishing scams.
For example:
- AI can generate fake or misleading information using natural language processing (NLP), such as fake news, fake reviews, fake testimonials, etc.
- AI can clone someone’s voice using speech synthesis, such as VALL-E, which can recreate a person’s voice after listening to them speak for only three seconds .
- AI can manipulate someone’s face using deepfake technology, such as DeepFaceLab, which can swap someone’s face with another person’s face in a video.
- AI can automate scams using chatbots, such as ChatGPT, which can generate coherent conversation based on human input.
These AI-driven scams can be hard to spot because they can mimic real people, situations, or events. They can also target specific individuals or groups based on their preferences, behaviors, or vulnerabilities.
On the other hand, AI can also be used to detect and prevent email and phishing scams.
For example:
- AI can analyze data using machine learning (ML), such as Cofense Triage, which can identify malicious emails based on patterns, indicators, or anomalies.
- AI can block malicious emails using spam filters, such as Gmail Spam Filter, which can filter out unwanted emails based on rules, reputation, or content.
- AI can report malicious emails using tools, such as Cofense Reporter, which can report suspicious emails with one click .
- AI can protect devices using antivirus software, such as Aura Antivirus which protects your device from malware infections .
These AI-driven solutions can help you spot and avoid email and phishing scams by providing you with more information, security, feedback, or protection.
However, AI is not perfect. It can also make mistakes, errors, or biases. It can also be hacked, corrupted, or misused. That’s why you need to be careful when using AI-based products or services. You should always verify the source, accuracy, reliability, and intention of any information or communication you receive online.
How to Spot Email and Phishing Scams
Spotting email and phishing scams can be challenging. They can look very similar to legitimate emails or messages. However, there are some clues that can help you identify them. Here are some things that you should check when you receive an email or a message that looks suspicious:
- Sender: Check the sender’s address and domain name for typos or inconsistencies. For example, if the sender claims to be from Microsoft but the address is microsoft@gmail.com instead of microsoft.com, it is likely a scam.
- Subject: Check the subject line for urgency, curiosity, or fear tactics. For example, if the subject line says “Your account has been suspended” , “You have won a prize” , or “You have been hacked” , it is likely a scam.
- Content: Check the content for grammar and spelling errors, impersonality, unfamiliarity, or requests. For example, if the content has many mistakes , does not address you by name , does not match your usual communication style , or asks you to do something unusual , it is likely a scam.
- Attachment: Check the attachment for suspicious extensions or destinations. For example, if the attachment has an .exe , .zip , .docm , .pdf , .jpg , etc., extension , it is likely a malware . If the attachment has a link that leads to an unknown or unsecured website , it is likely a phishing kit . Link : Check the link for suspicious extensions or destinations . For example , if the link has an .exe , .zip , .docm , .pdf , .jpg , etc., extension , it is likely a malware . If the link has a domain name that does not match the sender’s address or the website’s address , it is likely a spoofed website .

Some General Guidelines to Help you Spot Email and Phishing Scams
- Do not open or reply to unsolicited or suspicious emails
- Do not click on any attachment or link from unknown or untrusted sources
- Do not enter any personal or financial information on unsecured or spoofed websites
- Install a reliable antivirus software such as Aura Antivirus which protects your device from malware infections
- Use a spam filter such as Gmail Spam Filter which blocks malicious emails from reaching your inbox
How to Avoid Email and Phishing Scams
You can avoid email and phishing scams quite easily. You just need to follow some simple rules and best practices. Here are some tips on how to avoid email and phishing scams:
- Do not open any attachment or link from unknown sources
- Do not enter any personal information on unsecured websites
- You should use a password manager such as Microsoft Authenticator, Google Password Manager, LastPass, Dashlane which helps you store your passwords securely using encryption , autofill , 2FA , etc .
- Also use two-factor authentication such as SMS codes , email codes , phone calls , authenticator apps , biometric scans , etc., which adds an extra layer of security to your accounts
- Change your passwords regularly and update them if they are compromised
- Definitely report any suspicious emails using tools, such as Cofense Reporter which helps you report malicious emails with one click.
Conclusion
Emails and social media are one of the most common ways of communicating online. They can also be one of the most dangerous ways of getting scammed online. That’s why you need to know how to spot and avoid email and phishing scams in future.
In this blog post, we shared some tips and insights on how to spot and avoid email and phishing scams in 2023 and ahead. We have also explained what email and phishing scams are and how they work, what some common types and examples of email and phishing scams are like, what are the potential consequences of falling for them, and how AI can be used for or against phishing and scamming.
We hope this blog post will help you understand why online security matters and how to protect yourself from email threats. By following these tips, you can enhance your online security while enjoying the benefits of online communication.

Great article on how to spot and avoid email and phishing scams! It’s important to stay vigilant and protect ourselves from cyber threats.
Truly appreciate your well-written posts. I have certainly picked up valuable insights from your page.
Thank you Felix for your supportive words.