You have enabled HTTPS, but is your Blogger blog really secure?
That little padlock in your browser’s address bar is a fantastic first step, signaling that the communication between your readers and your blog is encrypted. However, in today’s digital landscape, securing your online presence, especially your valuable Blogger blog, requires a much more comprehensive approach.
We understand the fear of your blog being hacked, losing your hard-earned content, or even having your associated Google account compromised. You’re not alone in feeling uncertain about the specific security measures you should take for your Blogger platform.
That’s why we have put together the essential blogger security tips that go far beyond just enabling HTTPS. We’ll delve into actionable steps tailored for Blogger users, helping you fortify your blog and protect your digital home.

Table of Contents
Why Your Google Account is Your Blog’s Front Door
Think of it this way; your Google account is the key to everything on your Blogger blog. It’s the gateway that allows you to post your brilliant thoughts, manage your blog’s appearance, and interact with your readers.
If a malicious actor manages to get their hands on your Google account credentials, they essentially have free rein over your entire blog. They could vandalize your content, impersonate you, or even delete your blog entirely. Therefore, the security of your Blogger blog is inextricably linked to the security of the Google account you use to manage it.
Robust Google account security practices are absolutely essential for protecting your Blogger blog.
Securing Your Google Account
Let’s reinforce that front door with some strong locks!
Strong, Unique Passwords
This might sound like basic advice, but it’s the first and most crucial line of defense. We cannot stress enough the importance of using strong and unique passwords for your Google account. What does a strong password look like?
It’s a combination of uppercase and lowercase letters, numbers, and symbols that’s difficult for anyone to guess. Avoid using personal information like your name, birthday, or pet’s name, and steer clear of common words.
Reusing passwords across multiple online accounts is like using the same key for your house, your car, and your office – if one lock is picked, they all become vulnerable. Make sure the password you use for your Google account is unique to it.
A simple tool like a random password generator can solve the problem.
If you find it hard to remember multiple complex passwords, consider using a password manager. These tools can generate strong, random passwords and securely store them for you, so you only need to remember one master password.
Check our article on Creating strong secure passwords for your accounts.
Two-Factor Authentication (2FA)
Imagine your password as the first lock on your door. Two-Factor Authentication (2FA) adds a crucial second lock. Even if someone somehow manages to figure out your password, they won’t be able to access your account without this second verification step.
We highly recommend enabling 2FA on your Google account. You have several options for this second step:
- Authenticator Apps: Apps like Google Authenticator or Authy generate time-sensitive codes on your smartphone that you’ll need to enter during login. This is a secure and convenient method.
- Security Keys: These are physical USB devices that you plug into your computer or connect wirelessly to your phone to verify your login. Security keys offer the strongest level of protection against phishing.
- Backup Codes: Google provides backup codes that you can generate and store in a safe place. Use these if you can’t access your usual second factor.
While SMS verification codes are an option, they are increasingly considered less secure than authenticator apps or security keys. Enabling 2FA provides substantial protection against unauthorized logins to your Google account, and by extension, your Blogger blog.
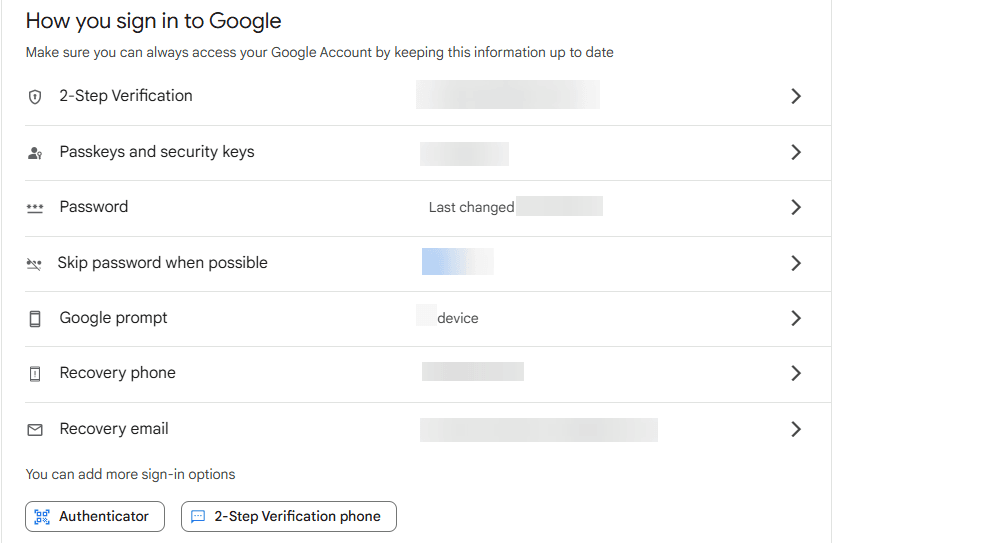
Keeping Your Recovery Options Updated
Think of your recovery email and phone number as emergency contacts for your Google account. If you ever forget your password or get locked out of your account for any reason, this information will be crucial for regaining access.
Make it a habit to regularly review and update your recovery email address and phone number in your Google account security settings. Ensure these are active and accessible to you.
Regular Security Checkups
Google provides a fantastic tool called Security Checkup that helps you review and manage your account’s security settings. We encourage you to use this tool regularly. It allows you to check:
- Connected Devices: See which devices are currently signed into your Google account and revoke access for any that you don’t recognize.
- Third-Party Apps with Account Access: Review the applications you’ve granted permission to access your Google account data and remove any that you no longer need or trust.
- Recent Security Activity: Monitor for any suspicious login attempts or other unusual activity.
By proactively monitoring your account activity, you can identify and address any potential security threats promptly, further securing your Blogger blog.
Managing Blogger Permissions Safely
Blogger (blogspot) offers you granular control over who can interact with your blog. Understanding and managing these permissions effectively is a key aspect of your blog’s security.
Understanding Author vs. Admin Roles
Blogger has different roles with varying levels of authority:
- Authors: Authors can create and edit their own blog posts.
- Administrators: Administrators possess broader capabilities. They can add or remove other team members (authors and admins), modify blog settings and templates, and edit or delete any posts.

The Principle of Least Privilege
When it comes to granting permissions, the principle of least privilege is a golden rule. This means you should only grant team members the minimum level of access they need to perform their tasks. For instance, if someone is solely responsible for writing blog posts, grant them Author access, not Administrator access.
Giving Administrator access to individuals who don’t genuinely require it is risky. A compromised administrator account could lead to significant damage to your blog. Limit the number of administrators to only those you absolutely trust with full control over your blog.
Inviting Authors Securely
When you invite new authors or administrators, Blogger will send an invitation via email. Before sending an invitation, especially if you don’t know the person well, try to verify their identity through other means if possible.
Be cautious of unsolicited requests for author or admin access. You can invite team members in the “Permissions” section of your blog’s Settings.
Regularly Auditing Permissions
Make it a habit to periodically review who has access to your blog and their assigned roles. If someone no longer contributes to your blog, remove their access promptly. This simple step can significantly reduce potential security risks. You can manage and remove team members in the “Blog admins and authors” section under “Permissions” in your blog’s Settings.
What to Do if an Author Account is Compromised
If you suspect that an author’s Google account has been compromised, act quickly to revoke their access to your blog.
You can do this in the “Blog admins and authors” section of your blog’s Settings. While their previous posts will remain, they won’t be able to make any further changes.
It is a good idea to communicate with the author (through a secure channel if possible) and advise them to secure their Google account immediately by changing their password and checking for any suspicious activity.
Recognizing and Avoiding Phishing Attempts Targeting Bloggers
Phishing attacks are a common tactic used by malicious actors to steal your login credentials, including those for your Google account. These attacks often come in the form of deceptive emails, messages, or fake login pages designed to trick you into revealing your username and password. Bloggers, like you, need to be particularly vigilant as your Google account holds the keys to your creative work.
Common Phishing Scams Aimed at Bloggers
Be aware of these common phishing scenarios:
- Fake Login Pages: Attackers might create fake Blogger or Google login pages that look very real. They might send you a link to these pages, trying to get you to enter your credentials. Always carefully check the URL of any page asking for your login information and ensure it belongs to the official Google or Blogger domain (blogspot.com). Minor misspellings or unusual domain names are red flags.
- Collaboration Requests with Malicious Links: You might receive emails that seem like legitimate collaboration opportunities but contain links that lead to phishing sites or malware. Hover your mouse over links before clicking them to see the actual URL. If the URL looks suspicious or doesn’t match the purported sender, don’t click it.
- Fake Security Alerts: Be wary of emails or messages claiming there’s a security issue with your Google account and urging you to click a link to resolve it. Legitimate security alerts from Google will usually direct you to your account security settings directly through the official Google website, not through a link in an email.
- Blogspot-Based Phishing Attacks: Attackers are increasingly exploiting the Blogspot platform itself to host phishing pages. These fake websites often mimic the login pages of banks, e-commerce sites, or social media platforms. They might lure users with promises of rewards or free money. Always verify the URL of any Blogspot blog that asks for sensitive information.
Key Signs of Phishing Emails/Messages
Here are some telltale signs that an email or message might be a phishing attempt:
- Urgent Language: Phishing attempts often create a sense of urgency, trying to scare you into acting quickly without thinking.
- Suspicious Links: As mentioned before, hover over links to check the actual URL. Be wary of links that are shortened or contain unusual characters.
- Generic Greetings: Phishing emails often use generic greetings like “Dear User” instead of your name.
- Requests for Login Info or Personal Details: Legitimate services will never ask for your password or other sensitive personal information via email. Remember the rule: Nobody who should have your sensitive information will ever call and ask for it.
- Poor Grammar and Spelling: While scammers are getting more sophisticated, many phishing emails still contain grammatical errors or typos.
- Unexpected Password Reset Requests: If you didn’t request a password reset, ignore the email and definitely don’t click any links in it.
If you have any doubts about the legitimacy of an email or message, do not click on any links or provide any personal information. Instead, navigate directly to the official website of the service in question by typing the URL into your browser.
By being aware of these tactics and remaining vigilant, you can significantly reduce your risk of falling victim to phishing attacks and protect your Blogger blog and Google account.
To know more about phishing email with examples you can check our post, How to Spot and Avoid Email and Phishing Scams
Conclusion
Securing your Blogger blog is an ongoing process that requires a multi-faceted approach. While enabling HTTPS is a crucial foundation, it’s just one piece of the puzzle. By focusing on the security of your Google account – your blog’s front door – carefully managing Blogger permissions, and staying vigilant against phishing attacks, you can build robust layers of defence.
Remember these key security layers:
- Strong and unique Google account password.
- Enabling Two-Factor Authentication (2FA) on your Google account.
- Keeping your Google account recovery options up-to-date.
- Regularly reviewing your Google account security settings.
- Understanding and diligently managing Blogger author and administrator permissions.
- Being cautious and aware of phishing attempts targeting bloggers and Google users.
If not already done we encourage you to implement these blogger security tips to significantly enhance the security and safety of your blog. Security is not a one-time task; it’s an ongoing commitment. By staying informed and taking proactive steps, you can protect your creative work and your audience.
So, go ahead, log in to your Google account and your Blogger dashboard, and start reinforcing your blog’s defenses today.
If you are interested in the other settings within Blogger definitely check our comprehensive post The Ultimate Guide to Master Blogger Settings.
