Cybersecurity is not just a concern for large corporations or government agencies. Small businesses are also vulnerable to cyberattacks that can compromise their data, reputation, and operations. In fact, according to a report by Verizon, 28% of data breaches in 2021 involved small businesses, and only 18% of them had implemented basic security measures such as encryption or antivirus software. Moreover, the average cost of a data breach for small businesses was $3.62 million in 2021, according to IBM.
As technology evolves and cybercriminals become more sophisticated, small businesses need to be aware of the current and emerging cybersecurity threats that they may face.
In this 5th blog post in the cybersecurity series, we will highlight the top cybersecurity threats for small businesses in 2023 and provide some tips on how to mitigate them.

Table of Contents
Ransomware
Ransomware is a type of malicious software that encrypts the victim’s files or locks their devices and demands a ransom for their restoration. Ransomware attacks can cause significant disruption and damage to small businesses, as they may lose access to their critical data and systems, face legal liabilities, and suffer reputational harm.
Some examples of recent ransomware attacks on small businesses include:
- In the first half of 2022, there were approximately 236.7 million ransomware attacks recorded globally.
- Ryuk, with 180.4 million targets, SamSam, with 103.9 million targets, and Cerber, with 28.2 million targets, are among the most frequently reported strains of ransomware.
- 10 million people were affected by a ransomware targeting android users called Gift Horse Trojan.
To prevent and recover from ransomware attacks, small businesses should follow these best practices and tips:
- Back up your data regularly and store it in a secure location that is not connected to your network or devices.
- Update your software and systems with the latest security patches and fixes.
- Use antivirus and firewall software to protect your devices and network from malware infections.
- Educate your employees on how to spot and avoid phishing emails and malicious links that may deliver ransomware.
- Do not pay the ransom if you are attacked by ransomware, as there is no guarantee that you will get your data back or that you will not be targeted again.
- Contact a reputable cybersecurity service provider or law enforcement agency if you are attacked by ransomware and seek their assistance.
Some reputed cybersecurity service providers that can help you with ransomware protection and recovery include:
- Cipher CIS: A cybersecurity firm that provides holistic, white-glove services to protect companies from attackers. They offer a unique combination of deep cyber expertise with an understanding of physical and IoT security. They also provide ransomware response services that can help you restore your data and operations quickly and efficiently.
- CrowdStrike: A cybersecurity company that specializes in endpoint threat protection. They offer a cloud-native platform that can detect and stop ransomware attacks before they cause damage. They also provide incident response services that can help you recover from ransomware attacks and prevent future ones.
- IARM Information Security: A cybersecurity company based in India that provides end-to-end cybersecurity solutions for small and medium businesses. They offer a range of services such as cybersecurity audit and assurance, IT service management, business technology advisory, and cybersecurity training and support. They also provide ransomware prevention and recovery services that can help you secure your data and systems from ransomware attacks.
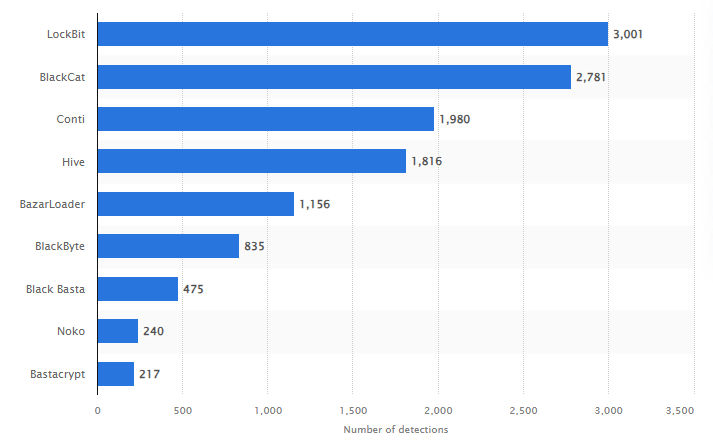
Data Breaches
Data breaches are incidents where unauthorized parties access or steal sensitive or confidential data from an organization or its customers. Data breaches can expose small businesses to various risks, such as identity theft, fraud, lawsuits, fines, regulatory penalties, and loss of trust.
Some examples of recent data breaches on small businesses include:
- India’s biometric database Aadhar containing the personal data of almost every citizen (nearly 1.1 billion people) was exposed in a security breach.
- In 2022, the average expense associated with a data breach in the United States reached $9.44 million.
- Ponemon Institute statistics indicate that a significant 77% of companies lack adequate preparedness and planning to effectively prevent and respond to attacks or data breaches.
To protect and secure data, small businesses should follow these best practices and tips:
- Encrypt your data at rest and in transit, using strong encryption algorithms and keys.
- Use strong passwords and change them regularly, avoiding common or easy-to-guess passwords.
- Implement multi-factor authentication for accessing sensitive data or systems, such as email, cloud services, or online accounts.
- Train your employees on how to handle data securely and responsibly, such as not sharing or storing data on unsecured devices or networks, not clicking on unknown links or attachments, and reporting any suspicious activity or incidents.
- Comply with the relevant data protection laws and regulations, such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA), and inform your customers about how you collect, use, and protect their data.
Some reputed cybersecurity service providers that can help you with data protection and security include:
- VP Techno Labs: A cybersecurity company with a team of one employee. Based in Nadiad, India, they were founded in 2019. Their services include cybersecurity, IT managed services, and web development for mainly small businesses. They also provide data security and privacy services that can help you safeguard your data from unauthorized access or theft.
- The Word Counter: A dynamic online tool used for counting words, characters, sentences, paragraphs and pages in real time, along with spelling and grammar checking. They also provide data encryption and decryption services that can help you protect your data from prying eyes or hackers.
- XenonStack: A product engineering and technology services company based in Chandigarh, India with a second office also located in India, and a third in San Francisco. Founded in 2012, the team of 19 specializes in BI and big data consulting and SI, cloud consulting and SI, and blockchain. They work primarily with midmarket clients in healthcare and medical, and information technology industries.
To detect and remove malware, small businesses should follow these best practices and tips:
- Scan your devices and network regularly with reputable security software that can detect and remove malware infections.
- Avoid suspicious links and attachments that may deliver malware to your devices or network.
- Use reputable sources for downloading software or apps and verify their authenticity before installing them.
- Disable or limit the use of removable media such as USB drives or external hard drives that may carry malware from other devices or networks.
- Update your software and firmware with the latest security patches and fixes that can prevent malware from exploiting known vulnerabilities.
Some reputed cybersecurity service providers that can help you with malware protection and removal include:
- Kaspersky: A cybersecurity company that offers a range of solutions for small businesses, such as antivirus, endpoint security, cloud security, and mobile security. They also provide malware analysis and incident response services that can help you identify and eliminate malware threats.
- SecureList: A cybersecurity company that provides threat intelligence and research services for small businesses. They also provide malware detection and remediation services that can help you protect your data and systems from malware attacks.
- The VP Techno Labs: A cybersecurity company with a team of one employee. Based in Nadiad, India, they were founded in 2019. Their services include cybersecurity, IT managed services, and web development for mainly small businesses. They also provide malware protection and removal services that can help you safeguard your devices and network from malware infections.

Denial-of-Service Attack
Denial-of-service attacks are attacks that aim to disrupt online services and websites by overwhelming them with traffic or requests from multiple sources. Denial-of-service attacks can cause downtime, slowdown, or loss of revenue for small businesses that rely on online services and websites to operate or serve their customers.
Some examples of recent denial-of-service attacks on small businesses include:
- The United States was the target of approximately 35 percent of distributed denial of service (DDoS) attacks in 2021.
- In 2022, Cloudflare reported a significant rise of 67% in ransom DDoS attacks.
- In March 2022, a denial-of-service attack on a domain name system (DNS) service provider affected its customers’ websites and online services. The attack was carried out by using a technique called DNS amplification, which involves sending spoofed DNS queries to open DNS servers and amplifying the response traffic to overwhelm the target.
To prevent and mitigate denial-of-service attacks, small businesses should follow these best practices and tips:
- Monitor your network traffic and performance regularly and look for any anomalies or spikes that may indicate an attack.
- Use cloud-based services or content delivery networks (CDNs) that can provide scalability, redundancy, and protection against denial-of-service attacks.
- Implement load balancing and failover mechanisms that can distribute your traffic across multiple servers or locations and ensure continuity of service in case of an attack.
- Configure your firewall and router settings to filter out unwanted or malicious traffic and requests.
- Contact your internet service provider (ISP) or hosting provider if you are under attack and seek their assistance or advice.
Some reputed cybersecurity service providers that can help you with denial-of-service protection and mitigation include:
- Cloudflare: A cybersecurity company that provides cloud-based solutions for web performance and security. They offer a global network of servers that can protect your website or online service from denial-of-service attacks by absorbing the malicious traffic and delivering the legitimate traffic. They also provide analytics and insights on your web traffic and performance.
- Akamai: A cybersecurity company that provides cloud-based solutions for web delivery and security. They offer a global platform of servers that can protect your website or online service from denial-of-service attacks by distributing the traffic across multiple servers and filtering out the malicious traffic. They also provide visibility and control over your web traffic and performance.
- Imperva: A cybersecurity company that provides cloud-based solutions for web application security. They offer a cloud-based firewall that can protect your website or online service from denial-of-service attacks by blocking the malicious traffic and allowing the legitimate traffic. They also provide monitoring and reporting on your web traffic and security.
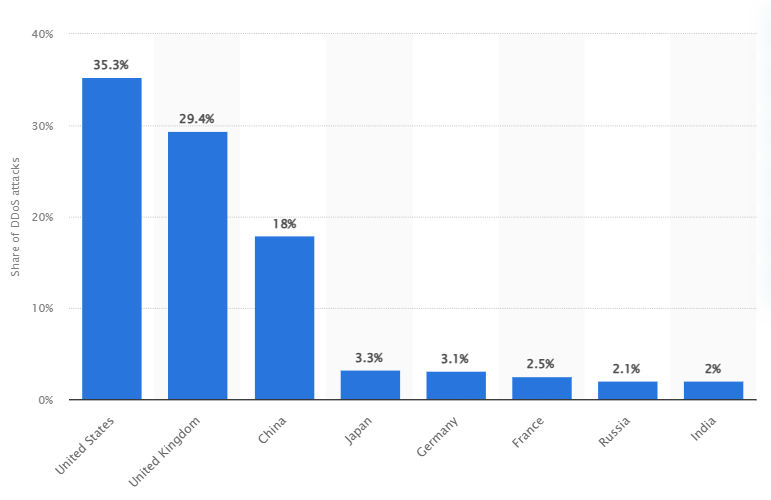
Conclusion
Cybersecurity is a vital aspect of running a successful small business. As cyber threats become more prevalent and complex, small businesses need to be proactive and vigilant in protecting their data, systems, and online services from cyberattacks. By following the tips and best practices we have shared in this blog post, you can reduce your cybersecurity risks and improve your cybersecurity posture.
However, cybersecurity is not a one-time effort or a one-size-fits-all solution. It requires constant monitoring, updating, and learning. That’s why we recommend that you also invest in cybersecurity awareness and education for yourself and your employees. By staying informed and updated on the latest cybersecurity trends, threats, and solutions, you can make better decisions and take smarter actions to safeguard your business.
We hope you found this blog post helpful and informative. We would love to hear from you and learn from your feedback.
Thank you for reading and stay safe online!





I very delighted to find this internet site on bing, just what I was searching for as well saved to fav
I frequently blog, and I truly value the stuff you provide. In fact, the piece has piqued my curiosity. I’m going to save your website to my bookmarks and keep coming back for fresh content.
Somebody essentially help to make significantly articles Id state This is the first time I frequented your web page and up to now I surprised with the research you made to make this actual post incredible Fantastic job
Hi my loved one I wish to say that this post is amazing nice written and include approximately all vital infos Id like to peer more posts like this